Designing a security system
In a security system, user membership is defined by user groups.
The user groups are associated with specific customers.
Figure 1 shows the elements used to design a security system. Each defect record in a security system references one or many customer records.
Figure 1. Elements of a security system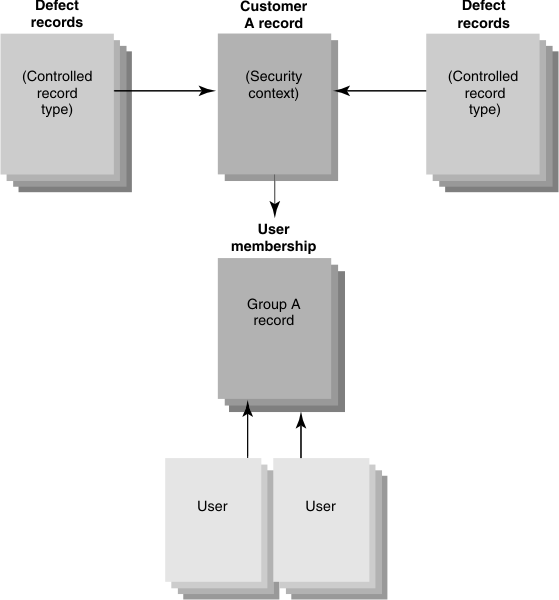

The security design in Figure 1 works in this way: User A logs in to the Rational® ClearQuest® environment. User A is a member of Group A, which is associated with Customer A. When User A runs a query or requests a record, all defects are filtered on the security context of Customer A. Only defects that belong to Customer A are included in the result set.